|
The Spyware
Warrior Guide to
Presenting
Anti-Spyware Scan Results
|
| |
|
|
| |
|
This page offers a discussion of the challenges that
anti-spyware vendors face in presenting scan results of detected
programs to users and the solutions that some of the leading vendors
have developed and adopted.
On this page...
Last revised: 30 May 2005
|
| |
|
|
| The Challenge to
Anti-Spyware Vendors [return
to top] |
| |
|
|
| |
|
Much of the discussion surrounding anti-spyware
applications has focused on what kinds of potentially unwanted software
ought to be detected and removed by such anti-spyware applications.
While this question or issue is an important one, it represents only one
of two related issues that anti-spyware vendors must grapple with.
- Threshold: threshold questions center on what criteria
anti-spyware vendors use to determine whether or not a potentially
unwanted software program will be offered to users for detection and
removal.
- Presentation: presentation questions center on how those
detected programs are presented to users for potential removal.
To date, the question of presentation has received much less
attention than the question of threshold (which is usually couched as the
question of what the definition of "adware" or
"spyware" is). Anti-spyware vendors are increasingly
struggling with methods for presenting scan
results to users, though, especially when users make several different, yet competing demands of
anti-spyware vendors with regard to programs that prove
"controversial."
If anti-spyware vendors are to serve their customers and users
effectively, they will need to devote more attention to the difficult
and occasionally contradictory demands and expectations of their users.
They will also need to recognize that the broad class of potentially
unwanted software they target in their applications requires a more
flexible set of methods for presenting detected programs to those users.
The Competing Demands of Users
Most anti-spyware programs scan users' PCs and present a complete
list of detected items to users at the end of the scan process. Such a
list of scan results can prove troublesome, though, because users make
competing demands of such scan results.
On the one hand, users are easily bewildered and overwhelmed by lists
of hundreds of detected adware and spyware items -- an outcome which is
not uncommon even on a moderately infested PC. Thus, many users insist
that they want simple, easy-to-understand scan results that don't force
them to make difficult too many difficult decisions. They simply want an
anti-spyware program to detect and remove everything on their PC that is
"bad," effectively pushing anti-spyware vendors to make a good
set of default judgments and choices and to present those choices in a
format that doesn't require too much knowledge on the part of the user.
On the other hand, many users also demand that anti-spyware programs
provide them guidance and information about the programs that are
detected on their PCs. While many users simply don't want to be burdened
with any decisions during the scan and removal process, others want to
learn more about the software installed on their PCs. These demands push
anti-spyware vendors to provide more information, not less, in the scan
results presented to users.
Still further, anti-spyware vendors are saddled with the challenge of
figuring out how to detect and present programs that even their own
customers and users disagree about -- "controversial" programs that
some customers may
find useful and may have deliberately installed but which other
customers may find problematic and objectionable.
Thus, anti-spyware vendors have been forced to figure out ways to
present more information to users while presenting that information in
an easier-to-understand, simpler format that doesn't overwhelm users or
induce them to make poor decisions. They have also struggled with
finding ways to satisfy users with contradictory expectations for the
detection and removal of certain "controversial" programs.
Revamping Scan Results
Over the past few years the top anti-spyware vendors have been
revamping their scan results, simplifying the presentation of detected
items, while adding more information to help users make better sense of
what the program has found on the PC. In order to make these scan
results more useful and understandable, vendors have begun implementing
several changes and improvements to the scan results presented to users.
- Tree-menu results: vendors have started grouping detected items by "family"
or "program" on an expandable tree of scan results, thus reducing the initial number of items
presented to the user and making relationships among items easier to
spot.
- More info: vendors have also started providing additional information about
the detected programs or families to help users understand the
functionality and potential risks of those programs.
- Special info: some vendors have even begun incorporating other types of
information, such as a "risk level" and "recommended
action."
This new information adds to the types of information that
anti-spyware vendors have typically provided about detected items, such
as the item type (file, folder, process, Registry key), location (file
path, Registry location, etc.), and program type (toolbar, BHO, program,
browser hijacker, etc.).
Revamping the Context of Presentation
To address all these challenges, it won't be enough for anti-spyware
vendors merely to revamp the traditional scan results screen presented to
users, though. Spyware vendors are increasingly being asked to detect a
wide variety of programs that prove "controversial" for any
number of reasons. In most cases, these programs are
"controversial" because users and customers may regard them
differently and may have contradictory expectations for whether they
should be detected and removed. In such cases, it is legitimate for
anti-spyware vendors to offer these programs for detection and removal
to users, but they need to be presented to users in ways that
accommodate the contradictory demands and expectations of users.
Two broad types of programs in particular stand out as potentially
"controversial":
- Low risk advertising programs: some users do voluntarily
and knowingly install advertising programs that are, comparatively
speaking, innocuous. While these programs do display advertising of
some sort on the user's desktop, the advertising is relatively
non-aggressive and well-labeled. Moreover, these programs tend to be
installed with the user's knowledge, often to support the free use
of some program that the user desires. Nonetheless, given the
functionality (advertising, data collection and transmission), there
will be some users who want such programs offered as a detection.
Thus, while some users may not want these
"low risk advertising programs" detected and removed,
others will.
- Potentially dangerous utilities: some users may install
system and networking utilities that can be put to a wide variety of
uses -- some legitimate, some not. When voluntarily and knowingly
installed and used, these utilities can prove to be valuable tools.
When installed without the user's knowledge and consent and used for
nefarious purposes by parties other than the user, these tools and
utilities can be dangerous and destructive. Again, some users may
not want such "potentially dangerous tools and utilities"
detected and removed; others will.
To handle these kinds of "controversial" programs and
respect the contradictory expectations of users, vendors will need to change the context in which
scan results are presented to users, and this involves much more than
simply tweaking the format of scan results or even revising the types of
information included in scan results.
In presenting such programs to users, the goal for vendors is to
alert users to presence of such programs on their PCs and to offer users
information to help them make good decisions about whether to remove
them. In doing so, though, vendors need to present these programs in
such a way that suggests to users that these programs do not exhibit the
same characteristics as the "spyware" and "adware"
traditionally detected by anti-spyware programs and that users can elect
to keep such programs, provided users understand those programs and
actually desire to keep them.
What anti-spyware vendors will ultimately need to do is develop new
methods for presenting a wide variety of different detected programs to
users, and these methods will need to go beyond merely presenting
detected programs as "spyware" or "adware." To date
vendors have developed at least three methods for changing the context
of presentation to go beyond the traditional scan results used by
anti-spyware programs.
|
| |
|
|
| Revamping Scan Results
[return to
top] |
| |
|
|
| |
|
What follows is a menu of examples of scan results as
presented in some of the leading anti-spyware programs.
- Spybot Search & Destroy
- PC Tools Spyware Doctor
- CA Pest Patrol 5
- Sunbelt CounterSpy
- Webroot Spy Sweeper
- Intermute SpySubtract
- McAfee AntiSpyware
- Lavasoft Ad-aware
|
| |
|
|
| 1. |
|
Spybot Search & Destroy |
| |
|
|
| |
|
Spybot Search & Destroy was the first major
anti-spyware application to simplify the scan results for users. Notice
how the results are reported by primarily application (e.g.,
WurldMedia, C2.lop, PeopleOnPage). Users can expand each application to see details on
the particular files and Registry keys associated with each detected
application.
-
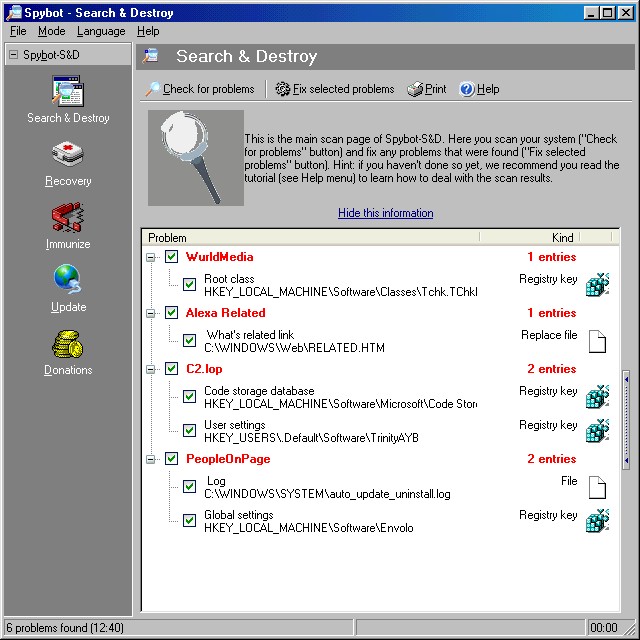
|
| |
|
|
| 2. |
|
PC Tools Spyware Doctor |
| |
|
|
| |
|
The latest version of PC Tools Spyware Doctor incorporates
much the same approach to reporting detections:
-
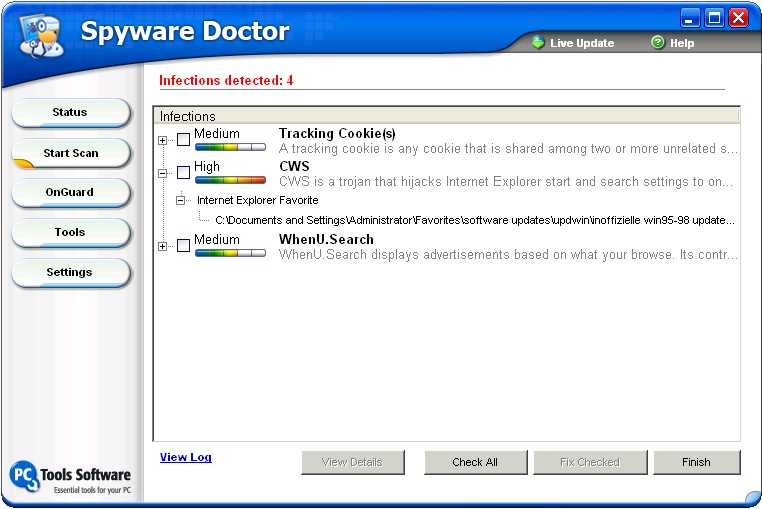
|
| |
|
|
| 3. |
|
CA Pest Patrol 5 |
| |
|
|
| |
|
The same holds true for Pest Patrol 5 (the latest version
from Computer Associates):
-
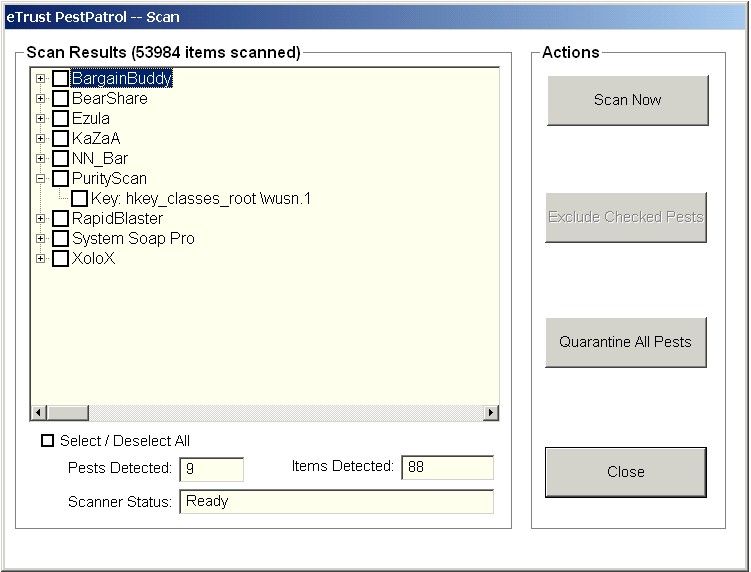
|
| |
|
|
| 4. |
|
Sunbelt CounterSpy |
| |
|
|
| |
|
Sunbelt CounterSpy takes the expandable tree-menu of
detected applications one step further by incorporating a drop-down menu to allow users to select actions to
perform on the detected applications:
-
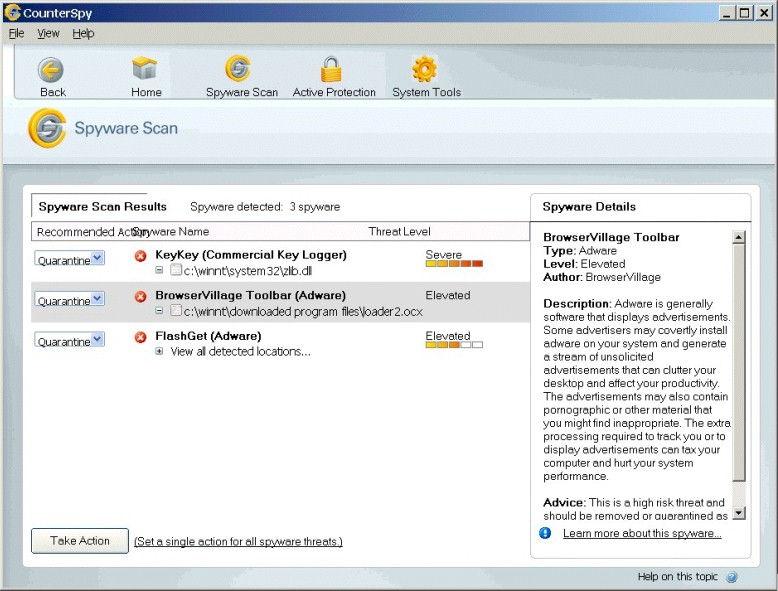
Notice also how information about the detected applications is
presented right alongside the scan results (an idea borrowed from Spybot
Search & Destroy). As Microsoft AntiSpyware, like CounterSpy, is
also based on the GIANT code base, it presents scan results in a
similar fashion. |
| |
|
|
| 5. |
|
Webroot Spy Sweeper |
| |
|
|
| |
|
Webroot Spy Sweeper reports detections in two steps.
First, it presents a scan results summary:
-
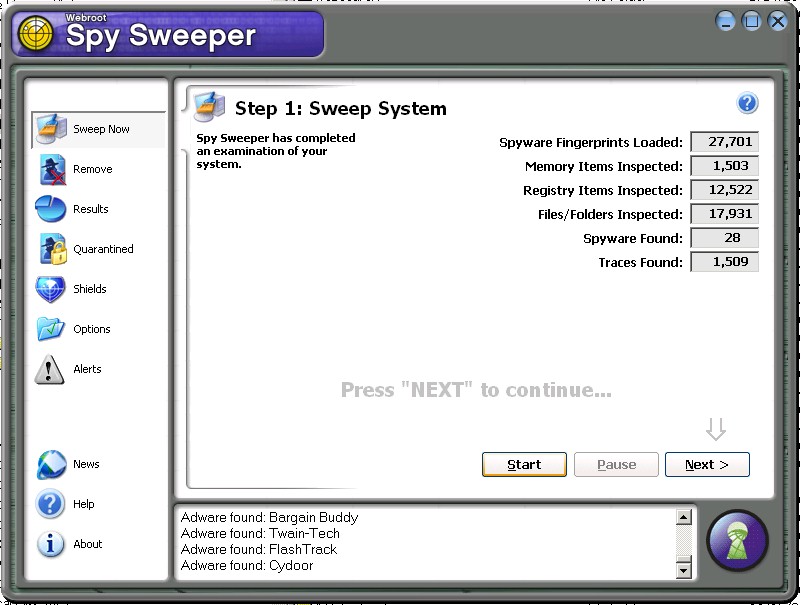
|
| |
|
Next it presents a tree-menu breakdown of the detected
applications:
-
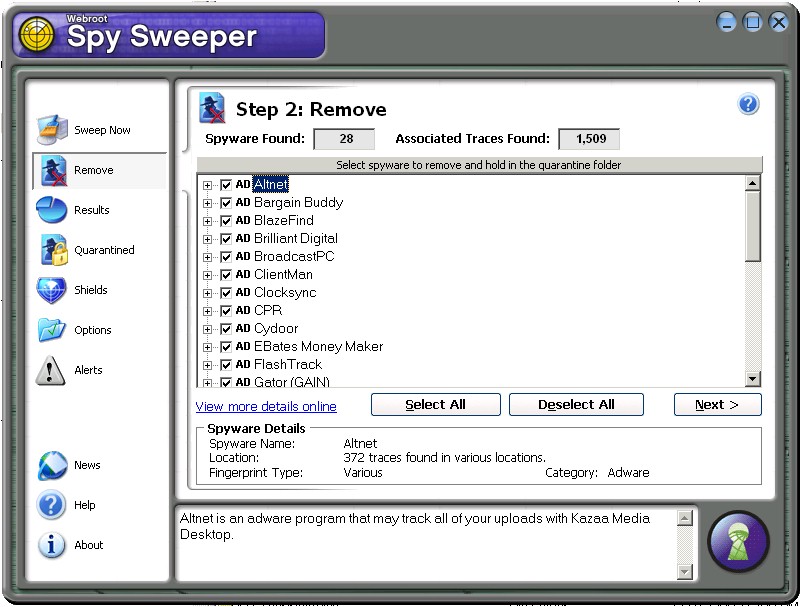
|
| |
|
This use of a summary screen followed by a tree-menu
breakdown of scan results is a kind of hybrid borrowing from Lavasoft
Ad-aware (which also uses a two-step approach) and Spybot Search &
Destroy (which uses the tree-menu scan results). |
| |
|
|
| 6. |
|
Intermute SpySubtract |
| |
|
|
| |
|
Intermute's SpySubtract uses an approach similar to Spy
Sweeper. First, the user is presented with a scan summary tab:
-
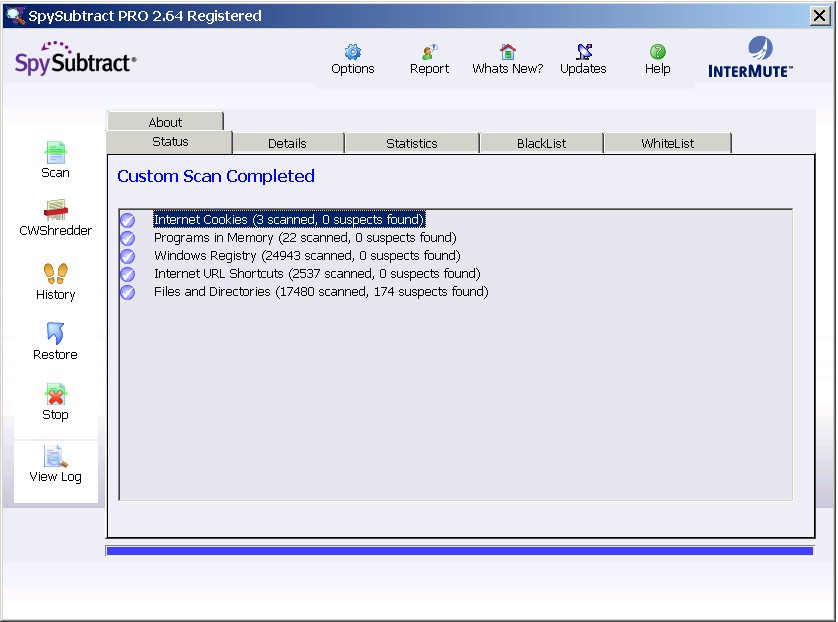
|
| |
|
Next the user is presented with a tree-menu breakdown of
the scan results:
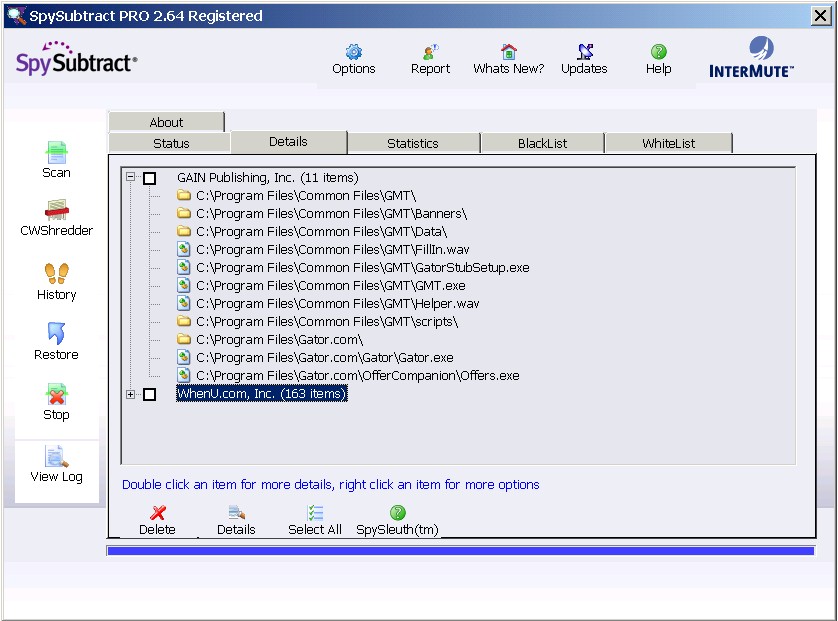
|
| |
|
|
| 7 |
|
McAfee AntiSpyware |
| |
|
|
| |
|
McAfee takes a slightly different approach to presenting
scan results. Like the other major applications, it groups detections by
application or family:
-
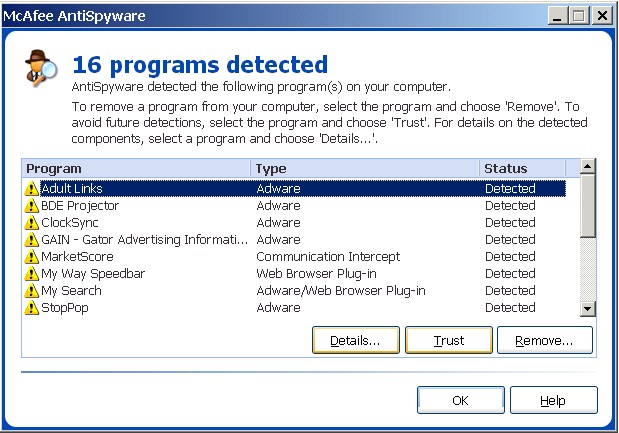
Unlike the others, though, McAfee allows users to highlight an
application and click the "Details..." button for information
on the particular Registry keys and files associated with the detected
application. Those details are presented in a separate pop-up box:
-
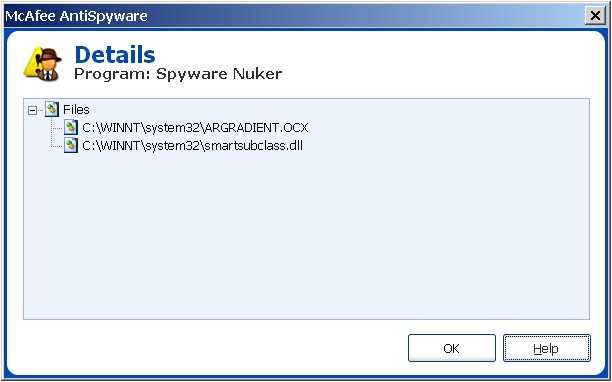
|
| |
|
|
| 8. |
|
Lavasoft Ad-aware |
| |
|
|
| |
|
Lavasoft Ad-aware is the grand-daddy of all dedicated
anti-spyware applications (version 1.0 came out in the fall of 2000), and its method for presenting scan results
has been evolving over the past few years, though slowly.
First the user is given a scan
results summary:
-
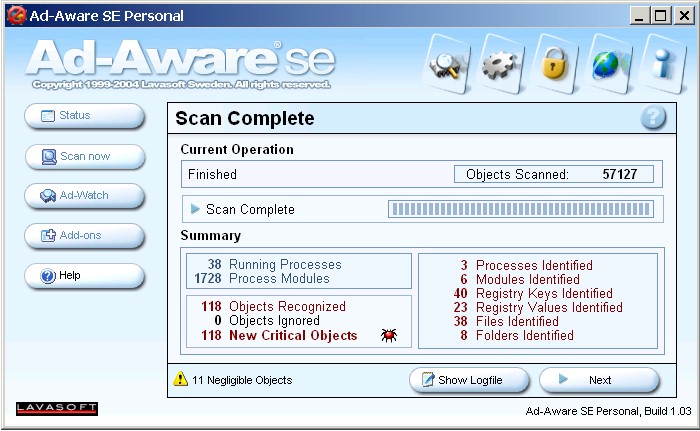
|
| |
|
Next, the user is presented with the "Scan Summary" tab,
which offers a kind of
tree-view summary of detected applications and other items:
-
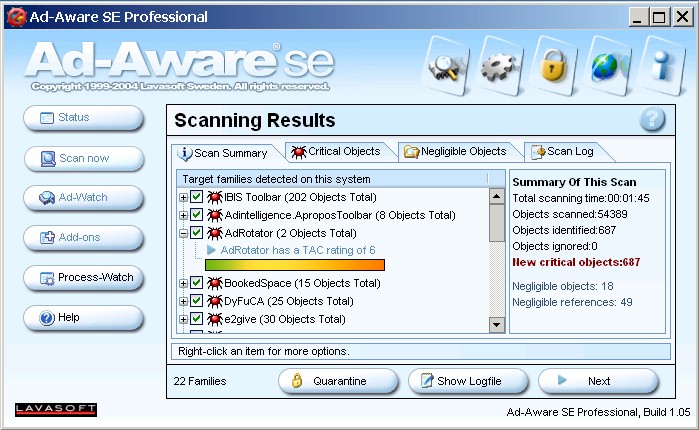
Unlike the tree-view summaries in other anti-spyware applications,
Lavasoft's "Scan Summary" tab does not include the details of detected items -- those
appear separately on the "Critical Objects" tab. In Ad-aware
SE versions prior to 1.0.6, this tree-view summary was not selected for the user by default
-- the
"Critical Objects" tab was selected instead.
To view more information about detected "spyware" and
"adware," the user can click the "Critical Objects"
tab for a more detailed scan results list:
-
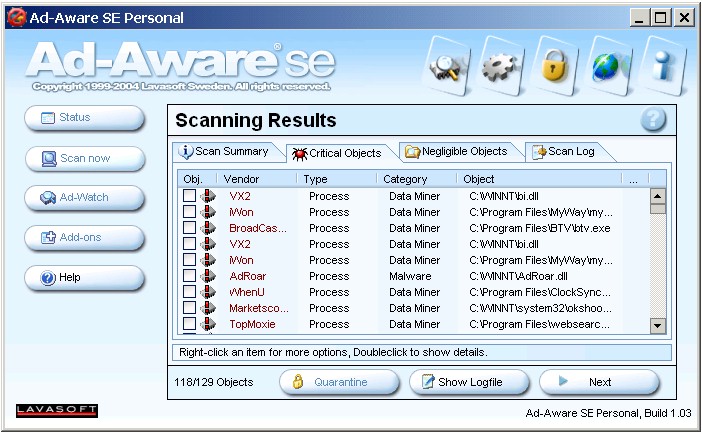
These results are sortable by "Vendor," but the results are
presented in one flat list, unlike the tree menus used by so many of the
other reputable vendors. I would expect Lavasoft to move to a more
manageable scan results screen in upcoming versions because this kind of
flat list of scan results can prove overwhelming to many users.
Summary
In one way or another, then, all of the reputable anti-spyware
vendors have been experimenting
with presenting scan results in a way that satisfies both non-expert
users (who want simple, digestible information) and expert users (who
want a wealth of detail about what specifically the application has
detected). For now, the tree menu seems to be the most popular means for
accommodating both types of users. |
| |
|
|
| Revamping
the Context of Presentation [return
to top] |
| |
|
|
| |
|
Anti-spyware vendors have developed at least three ways to
handle potentially "controversial" programs and present them
to users:
- The Pre-Populated
White List/Black List
- Multiple Scan
Tabs
- Include/Exclude
Special Detections
|
| |
|
|
| 1. |
|
The Pre-Populated White List/Black List (SpySubtract,
Spybot Search & Destroy) |
| |
|
|
| |
|
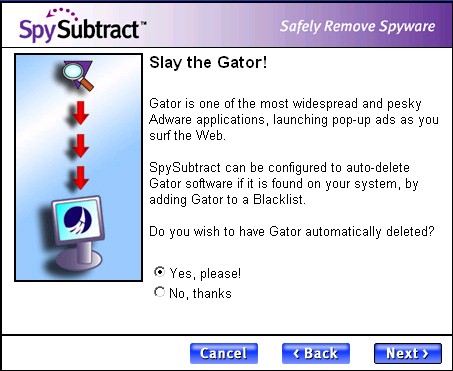
SpySubtract uses what can be called a "pre-populated
black list/white list." Most anti-spyware programs allow users to
add certain programs or detections to an "ignore list" to exclude
them from future detection. SpySubtract takes this idea one step further
by building an "ignore list" during installation.
First, during installation SpySubtract presents short descriptions of "controversial" programs to the user and explicitly asks users whether they want
to detect and remove such programs.
SpySubtract then stores users' preferences on its "Black List"
and "White List" tabs:
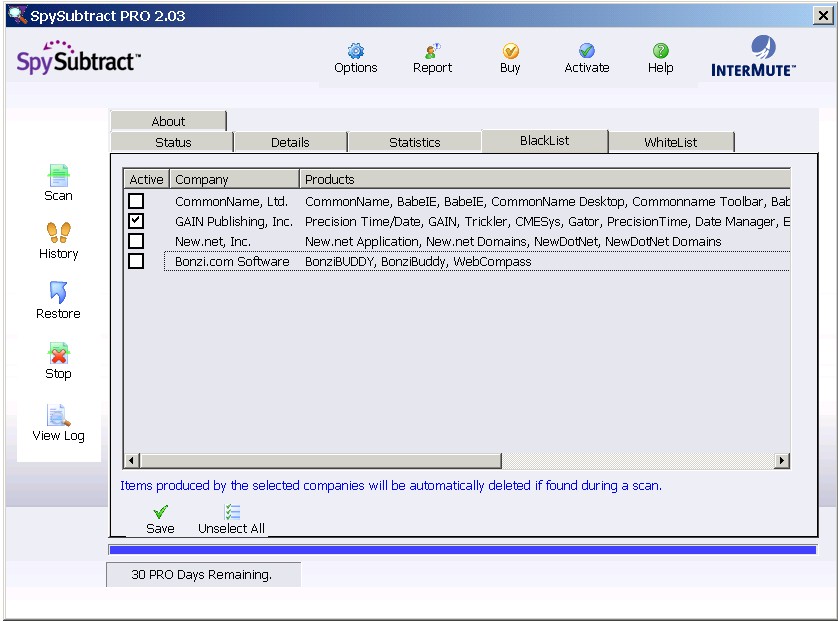
Notice that this "Black List" is pre-populated with several
programs, which users can elect to detect by checking the boxes.
Programs listed in the "Black List" will not be detected
unless users affirmatively elect to detect such programs by checking the
appropriate boxes. Users can add other programs to the "White
List," which excludes programs from detection and removal.
This pre-populated "White List"/"Black List" allows SpySubtract to offer
a range of "controversial" programs for detection and removal,
but only to users who actually want such programs to be targeted by
SpySubtract.
SpySubtract wasn't the first anti-spyware program to use such a
"pre-populated white list/black list." Spybot Search &
Destroy has incorporated similar functionality for several years in its
"Ignore products" settings section. In the last few versions of Spybot
several products have been excluded by default from detection, though
users could choose to include such products in Spybot's scan and removal
process by unchecking the appropriate boxes. The problem with earlier
versions of Spybot, though, was that users were not warned that such an
"ignore list" was being used. Moreover, the excluded products
were spread across multiple tabs in the "Ignore products"
section, making them somewhat difficult to find.
The most recent beta of Spybot Search & Destroy 1.4 partially
addresses these problems by grouping such "controversial
products" on a separate tab labeled "PUPS.sbi" (PUPS
standing for
"potentially unwanted programs," a term borrowed from McAfee):
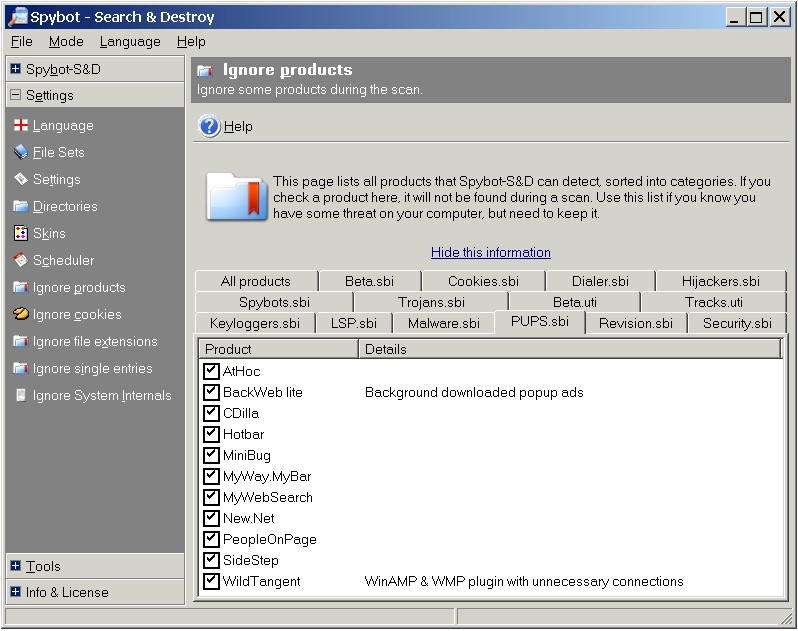
As with SpySubtract's "White List"/"Black List," Spybot's
"Ignore products" section allows the program to accommodate the competing
demands of users with regard to "controversial,"
"potentially unwanted programs."
|
| |
|
|
| 2. |
|
Multiple Scan Tabs (Ad-aware,
Aluria) |
| |
|
|
| |
|
Another method for changing the context of presentation
for scan results is to spread detected items across multiple tabbed scan
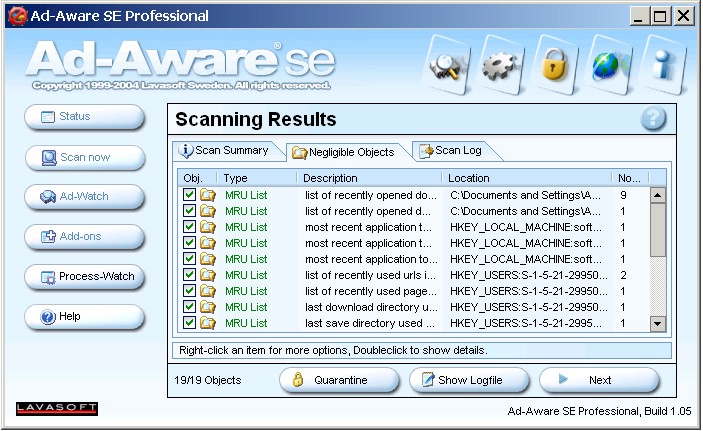
results pages. Ad-aware SE was the first major anti-spyware program to
do this, putting "Negligible Objects" (usually Registry data
about "most recently used" programs and files) on a separate
tab than "Critical Objects" (detected "adware" and
"spyware" programs).
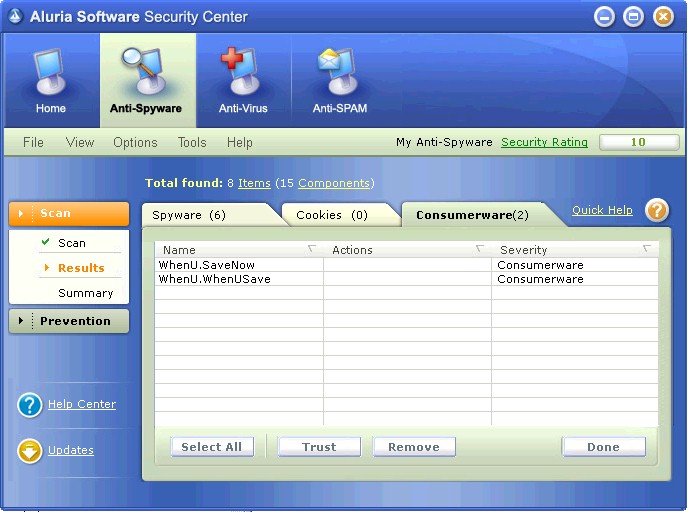
Aluria's most recent anti-spyware product, Aluria Security Center,
takes this idea one step further by putting cookies and low risk
programs (dubbed "Consumerware") on separate tabs than
detected "spyware," thus suggesting to the user that these
items have different qualities than "spyware" and should be
handled differently.
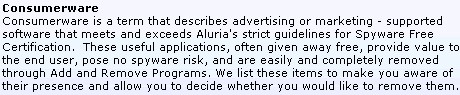
Aluria describes "Consumerware" thusly:
The goal with these separately tabbed scan results is much the same
as the "pre-populated white list/black list" that we saw
earlier: to continue to offer "controversial" detections to
users, but to present those detections in a different way that
accommodates the competing expectations of different users.
|
| |
|
|
| 3. |
|
Include/Exclude Special Detections (Spyware
Doctor, Ad-aware) |
| |
|
|
| |
|
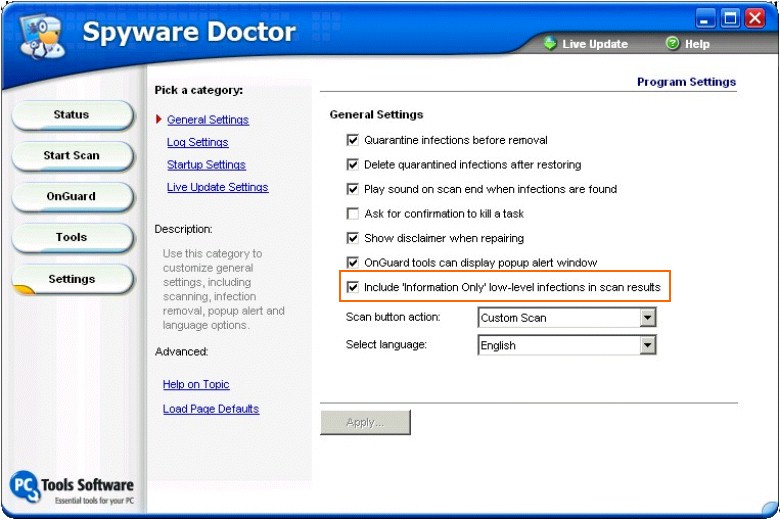
A third way to change the context of presentation is to
allow users to exclude a whole class of "controversial"
programs from detection and removal, such as the latest version of
Spyware Doctor does. Spyware Doctor 3.2 includes a checkbox that enables
users to "Include 'Information Only' low-level infections in scan
results":
The PC Tools web site describes
"Information Only" detections in terms similar to Aluria's
"Consumerware":

The problem at present is that users have no way of knowing what
particular programs are included in this category of "Info Only"
detections.
In version 1.0.6 of Ad-aware, Lavasoft also incorporated a similar
"Search for low-risk threats" checkbox.
-
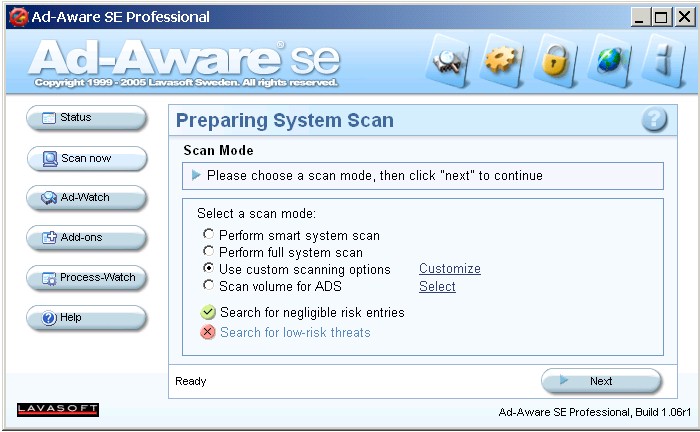
This checkbox is de-selected by default. As with Spyware Doctor, the
problem at present is that users have no way to find out just what
programs are covered by the "low-risk threat" category.
|
| |
|
|
| Some
Final Thoughts on Standardization
Among Vendors... [return
to top] |
| |
|
|
| |
|
In recent months there have been increasingly vocal calls
for anti-spyware vendors to collaborate on developing industry standard
names, definitions, and classifications for detected programs.
Standardizing Detections & Names
Standardization on some classification and naming
convention by anti-spyware vendors would indeed be most helpful. Such an effort
would necessarily focus on at least two goals:
- Standardizing names: that is, developing a common set of names for
the detections (much like AV vendors have a naming convention for
viruses and worms).
- Standardizing detections: that is, developing a common,
recognized list of components for particular adware/spyware
applications (e.g., VX2.Look2Me is comprised of XYZ files
and ABC Registry keys).
Standardizing names would certainly be the more easily achievable
goal, though even that would require significant work and coordination.
Standardizing detections would be much more difficult. One of the biggest obstacles to
the standardization of detections is the fact that
anti-spyware vendors currently regard their definitions databases as key
components of their competitive prowess, and standardization of
detections might mean divulging what they regard as semi-proprietary
knowledge.
One danger of any effort to standardize detections is that publishing a public set of detections would
inevitably facilitate the growth of disreputable anti-spyware applications, many of
which simply rely on publicly available data (e.g., from Pest
Patrol's web site, SpywareGuide.com, Kephyr.com, doxdesk.com, et al) to
plug into their definitions, thus allowing them to generate the semblance
of a decent scanning application without doing any substantive research
of their own.
Information Sharing from Advertising Software Vendors
Much the same problem afflicts proposals that adware/spyware
vendors share information about their applications so as to facilitate
standardized detections. Such vendors would
likely view such a proposal as tantamount to handing their
enemies the bullets for so many anti-spyware guns. Thus, I suspect they
would be willing to share such information only on the condition that it
be used as part of a de-listing process.
Even then, some of the worst actors out there (the CoolWebSearch gang
comes to mind) would likely never share information about their
applications, as their success in stealth-installing unwanted software
on victims' computers depends in part on their ability to generate new,
hitherto unrecognizable software components. Some of these entities
might even shun the danger of communicating with anyone, so deliberately
shadowy is their existence.
At best you would get spotty coverage from
such an effort, with a small number of well-documented adware
applications from "top-shelf" adware vendors and a vast mass
of muddily understood components from the borderline criminal gangs and
fly-by-night scam artists.
Standardizing Definitions of "Spyware" &
"Adware"
Some have also suggested that anti-spyware vendors develop a
standard set of definitions for terms such as "spyware" and
"adware." These calls usually come from the advertising
software industry itself. Such an effort would be less useful, I think,
because the terms "spyware" and "adware" have very
little use to begin with, being historical accidents of naming and
pointing only to a broad, loose class of potentially unwanted software
that defies easy classification.
What such advertising software vendors really want is a standardized
method for determining the threshold for offering a program as a
detection to users of anti-spyware programs. While it would certainly be
useful for anti-spyware vendors to discuss openly their thresholds for
offering programs as detections to their customers, ultimately
anti-spyware vendors must make their own decisions about how best to
serve their own user and customer bases, which can vary from vendor to
vendor.
Note: Anti-Spyware Vendors Under Scrutiny
Anti-spyware vendors are the target of greater scrutiny and
increased criticism, esp. from the advertising software industry.
Although advertising software companies have long compained about
anti-spyware vendors (see for example C2 Media's pissy
complaint to the FTC in advance of the FTC's 2004 Spyware Workshop),
these companies have honed their critique in recent months. Perhaps the
best example is this 84 page critique by Claria Corp. of the ways in
which anti-spyware vendors allegedly mistreat, misname, misclassify, and
misreport Claria's several applications:
-
Fighting Spyware and the Need for Anti-Spyware Standards
[PDF / 9.1 mb]
While there are legitimate complaints in that document, I can't help
but note that while adware firms have been loudly demanding that
anti-spyware vendors craft a clear, unified, objective set of standards
and definitions for advertising software, they have been unable to come
up with any standards themselves to police their own industry.
This, from the gang that has been loudly insisting to everyone with ears
for the past few years that "industry self-regulation" was
adequate to the task of solving the problem of "spyware."
|
| |
|
|
|
[return
to top]
© Copyright 2005 Eric L. Howes |
|